How to Perform Sqlite Windows File Forensics

Published: March 3rd, 2016 • 4 Min Read
In our last update we discussed about Linux Sqlite file structure and its forensic, so this time we discussed a new interesting topic that is Sqlite Window File Forensics. Evolution in technology has made us witness many such cyber crimes which would never have been solved without implementing digital expertise. Many of these crimes need to collect information from the systems belonging to various operating systems depending on the case. Digital forensics has become crucial part of the corporate arena and the trails left on the system while accessing, reading, viewing any file can help in tracking the criminal. Sqlite database forensics especially Sqlite Windows forensics has been part of the investigation since many applications and browsers store the data and searches in Sqlite databases. The very first step for such need is to know where the Sqlite databases are located exactly and how are these artifacts necessary.
Parsing Browsers & Application Sqlite3 Databases
Firefox on Windows OS
Firefox application, which is the most popular browser for users, stores much of the data in the Sqlite format. These databases are considered as great source for forensically rich data for crime investigation. The default location for Firefox storage in Windows Operating System is;
Windows XP: C:\Documents & Settings\User\ Application Data\Mozilla\Firefox\Profiles
Windows 7: C:\Users\Username\AppData\Local\Mozilla\Firefox\Profiles\<profile folder>
In this location, all the Sqlite databases are store sin a directory which is listed below;
- places.sqlite
- addons.sqlite
- chromeappsstore.sqlite
- content-prefs.sqlite
- cookies.sqlite
- download.sqlite
- search.sqlite
- extensions.sqlite
- signons.sqlite
- formhistory.sqlite
- permissions.sqlite
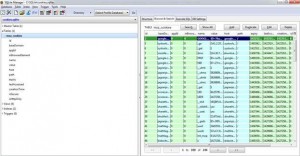
All these files comprise of important data like download.sqlite comprises of details about files which are downloaded using Firefox browser. moz_downloads table comprises of all the information stored about file name, source, date, size, referrer, location downloaded at, etc. This table can be easily viewed using Firefox add on Sqlite Manager. Image below displays the details of moz_cookies table, likewise all the databases can be viewed.
Google Chrome on Windows OS
Similarly, Google Chrome browser stores all the data related to the browser in Sqlite databases to some fixed locations. By default these locations are;
Windows XP: C:\Documents and Settings\User\Local Settings\Application Data\Google\Chrome\
Windows 7: C:\Users\Username\AppData\Local\Google\Chrome\
Skype on Windows OS
Skype is one of the applications which are used highly by users and investigator can consider Skype to be a source where a lot of information can be gathered. Chatting and social networking can actually bring out many details and despite of messages deleted at front end, database investigation can carve out important traces leading to crime intentions. Skype application also stores all the details in Sqlite databases and artifacts can be collected from below locations.
Windows XP: C:\Documents and Settings\Profile\AppData\Roaming\Skype\Skype User\main.db
Windows 7: Users\userprofile\AppData\Roaming\Skype\SkypeName\main.db
Once the databases are collected, we can utilize the command line program to view complete details of Sqlite databases. The following command can help to get all the details;
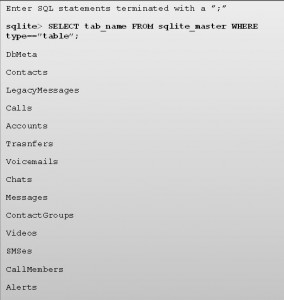
SELECT tbl_name FROM sqlite_master WHERE type==”table”
Sqlite database has a table named sqlite_master with a column named tbl_name. This describes all the tables of database. Using SELECT statement helps to view tables in Skype main.db database. This database will comprise of tables with information like; contacts, accounts, calls, messages, SMS messages, accounts, chat, etc.
Conclusion:
There are many such browsers like Firefox and applications like Skype whose data is stored in the Sqlite databases. These databases can be collected and can be viewed using Sqlite viewing applications like Firefox Sqlite Manager or Command line utility. Some third party utilities like Sqlite Viewer can also be utilized if the Sqlite databases are corrupted or user is not aware of executing Sqlite manager or command line utility. Sqlite Windows forensics can be done to all such programs and applications which are associated with the Sqlite database for storage which happens to be most suitable way for digital investigation.